There are more than 50 cybersecurity standards and frameworks. What is the best way to choose a solid and pragmatic cyber security framework? Choose the simplest and select the security measures that apply to your business needs!

Selection criteria
A framework should be used to measure and track your organization’s security posture. It is a tool that is used on a daily basis.
I reviewed dozens of information security guidelines and standards. In this analysis, I selected only generic ones. I have excluded security guidelines that are very specific to products or technologies.
Selected cybersecurity frameworks
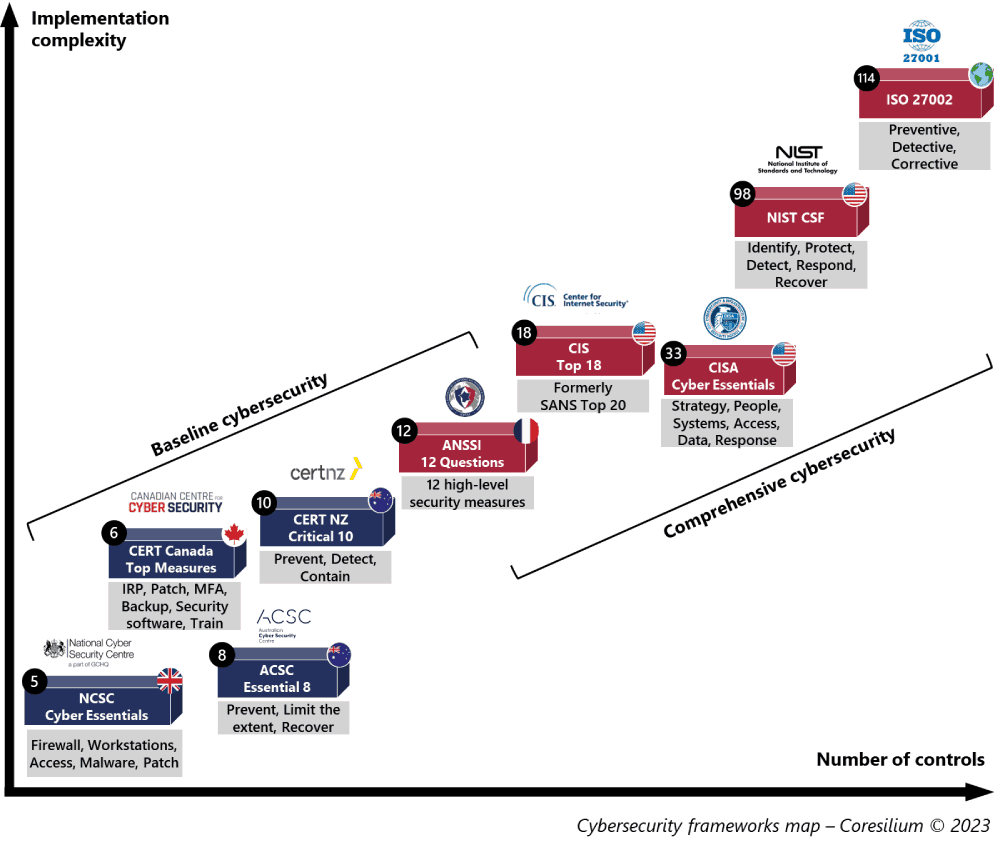
The complete list below is sorted by date of last update.
| ISO 27002:2022 ISO/IEC | 93 physical, human, organizational, technological measures, with 3 types of controls (Preventive , Detective , Corrective) and 5 concepts that are identical to NIST CSF . | February 2022 |
| Critical 10 CERT New Zealand | Checklist of 10 up-to-date and pragmatic critical controls to Prevent , Detect and Contain cyberattacks. | February 2022 |
| MITRE Engage Mitre Corporation | Matrix of 50 counter-offensive techniques to Expose , Affect and Elicit adversaries in 5 steps (Prepare , Expose , Affect , Elicit , Understand). – Formerly MITRE SHIELD. | March 2022 |
| Cyber Essentials National Cyber Security Center (UK) | 5 essentials technical and basic controls (firewall , workstations , access , malware , patch). Certifiable by the UK Government (CyberEssentials Plus). | January 2022 |
| ETSI TR 103 305-1 European Telecom Standards Institute | Standard based on the 18 measures of CIS Critical Security Controls v8 with 3 implantation profiles (IG) according to the desired level of security. | Dec. 2021 (v4.1.1) |
| ACSC Essential 8 Cyber Security Center (Australia) | List of 8 essential measures with 3 levels of maturity to Prevent , Limit the extent , Recover from a cyberattack. Pragmatic with prescriptive guides. | October 2021 |
| MITRE ATT&CK Mitre Corporation | Matrix of 218 offensive techniques organized into a 14-step attack life cycle . | October 2021 |
| MITRE D3FEND Mitre Corporation | Matrix of 117 defense strategies (Harden , Detect , Isolate , Deceive) in 15 categories. | June 2021 |
| CERT Canada Top Measures Center for Cyber Security (Canada) | 6 essential measures for small businesses, extracted from the 13 of the Baseline. | June 2021 (ITSAP.10.035) |
| CISA Cyber Essentials Cybersecurity and Infrastructure Security Agency (USA) | Clear and classified measures according to two responsibilities (management and IT) and based on 6 pillars ( strategy , people , systems , access , data , response ). | March 2021 |
| ANSSI Cybersecurity in 12 questions Information Security National Agency (France) | Framework for SMEs which combines 12 high-level and technical measures posed in the form of questions. | February 2021 |
| CIS Critical Security Controls Center for Internet Security | List of 18 critical security measures. Formerly SANS Top 20. | May 2021 (v8) |
| ISF Standard of Good Practice for Information Security 2020 Information Security Forum (UK) | 6 aspects (Governance, Applications, Workstations, Networks ,Systems , Users). Reserved for members (not free). | May 2020 |
| CERT Canada Baseline Cyber Security Controls Center for Cyber Security (Canada) | Set of 5 organizational measures and 13 technical and procedural measures (20% of security measures for 80% of benefits). Can be certified (CyberSecure Canada). | February 2020 (v1.2) |
| NIST Cyber Security Framework (CSF) National Institute of Standards and Technology (US) | Reference to measure the maturity of security controls and their alignment to organizational objectives. 108 controls et 5 functions (Identify, Protect, Detect, Respond, Recover). | April 2018 (V1.1) |
| ANSSI Guide d’hygiène informatique Agence Nationale de la Sécurité des SSI (France) | Book containing 42 essential computer hygiene measures divided into 9 categories. Not updated. | January 2017 |
Choose your cybersecurity framework
Prior to choosing a cybersecurity reference framework, it is important to consider your business sector and the applicable regulatory requirements. If so, you must use the applicable cyber security standard (health, energy, finance, etc.). However, for a mature organization, I recommend the NIST Cyber Security Framework (CSF). It is comprehensive, understandable and very well aligned with other standards and compliance requirements. The 5-area approach makes a lot of sense:
- Understand what to protect ( Identify )
- Implement protective measures ( Protect )
- Monitor and anticipate ( Detect )
- Manage incident ( Respond )
- Knowing what to do if things were to go wrong (Recover).
My approach
I essentially use NIST CSF and ISO 27002:2022. The new version of the ISO 27002:2022 standard – Information security, cybersecurity and privacy protection – Information security measures , was published in February 2022. The number of measures has been reduced to 93. They are structured in 3 types (preventive, detective, corrective) and in 5 concepts (identify, protect, detect, respond and recover). This structure corresponds exactly to the NIST CSF domains.
Simplified frameworks
For SMEs/SMIs, there are good practice guides, notably produced by Australia (Essential 8), New Zealand (Critical 10), Canada (Baseline Security Controls) or the United States (Cyber Essentials). The measures are up-to-date, concise and very useful for smaller structures. The ANSSI guides from the French government (the 12 questions or 42 measures) are written in an editorial style. These two guides are more difficult to translate into concrete actions.
Advanced frameworks
When it comes to structuring defensive security operations for more mature organizations, I use MITRE D3FEND. This framework is aligned as a response to MITRE ATT&CK which is a reference in the field. The new MITRE ENGAGE matrix is based on a counter-offensive approach which is applicable for the most advanced companies in their cyber defense operations.
As for the levels of maturity, I use the guide of the European Agency for Cybersecurity (ENISA NCAF). It contains an accurate and highly researched description of maturity and capabilities. Although this document applies to EU member countries, I use their very rigorous methodology to formalize security maturity assessments.