Considering the risks of IT disasters, outages, and cyber attacks, you must be prepared. There are many acronyms to describe the contents of a Business Continuity Plan (BCP). Knowing where to start and what type of continuity plan will work best for you is essential.

Large companies have the ressources to set up dedicated teams for each function of their continuity plan. However, this is not possible for a smaller organization.
There are about ten terms to define operational and IT response plans. So, where to start? The key is to have a simple and operational plan, whatever you call it.
Keep it simple and pragmatic
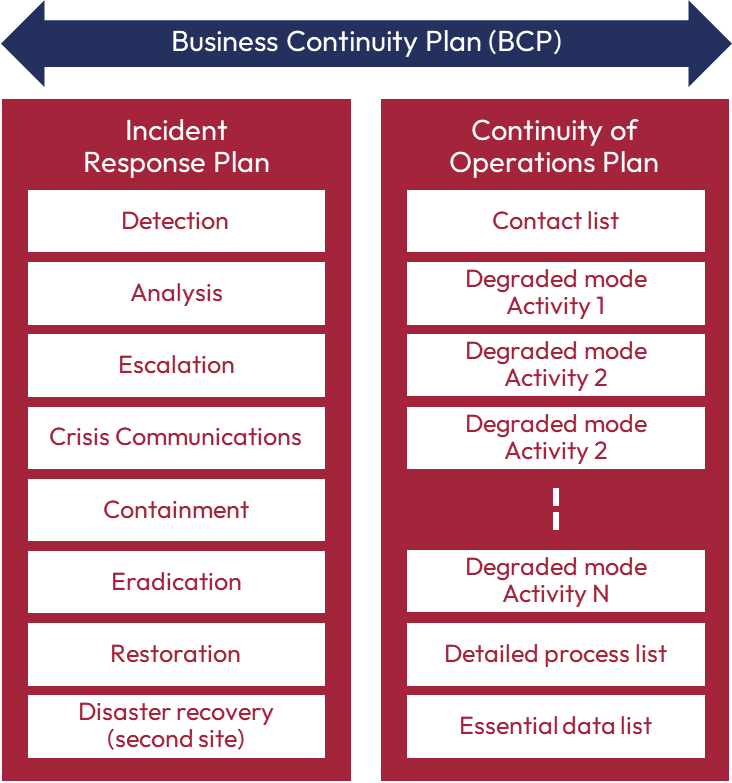
Define a unique plan that you can call for example “Incident Response Plan” or “IT Contingency Plan”. In this document, include the following essential elements:
- Essential contacts (and alternates) that you can reach with your mobile phone, even without IT (IT teams, operations, human resources, communication, service providers, etc.).
- Main tools for detecting an incident (security tools, alerts, consoles, or the reporting procedure by users)
- Quick incident analysis matrix to identify what is impacted and the level of severity
- Escalation flowchart to know who communicates with whom and when in a crisis situation (employees, suppliers, customers, partners)
- Simple instructions to contain and eradicate the incident (ex. disable remote access, change passwords, check backups, etc.)
- Recovery procedure (system recovery order, data restoration, deployment of a clean image on compromised workstations, etc.)
What will you do if it is impossible to quickly restore your IT systems?
Plan the actions to be taken if the computer systems were to be unavailable for a long period (several days or weeks). In this case, write a second document with the business process owners (Operations Continuity Plan).
Simply identify the most critical business processes in your organization. Is it possible to switch to manual or paper mode? If so, document it. If this is not possible, then describe what the affected employees will be able to do to minimize the impact on the business (reallocation of resources, communications with customers, related tasks, etc.).
In the event of a major crisis, you can then trigger this business-level business continuity plan while IT teams work to restore systems.
What should I do if my server room is destroyed?
The risk of disaster exists both on your sites and in the cloud. So, document how your infrastructure can be restored in the event of an interruption:
- Systems failover (or restoration) to an alternate site (or zone/region in the Cloud)
- Failover your Internet access and telephony links to a backup link (or another technology, such as 4G or 5G).
This Disaster Recovery Plan (DRP) will be triggered in the event of a disaster. In addition, plan a disruptive cyber attack scenario (e.g. ransomware). In this case, you will not be able to simply restore your systems as they are. A clean reinstallation step will be necessary before copying the data (files, databases) from the backups.
In summary, get ready!
To be prepared, write a primary incident response document and a separate one for business operations continuity. The computer incident response plan can integrate restoration or switch procedures to a spare infrastructure in the event of a disaster.
In the case of a cyber attack, the detection, containment and eradication steps are specific. For a fire or a flood, eradication is quite straightforward. Unlike cyber attacks, there is no persistence of the threat in the IT environment following an accidental or natural disaster.